Static Application Security Tool
CODEMIND CSI/CQI
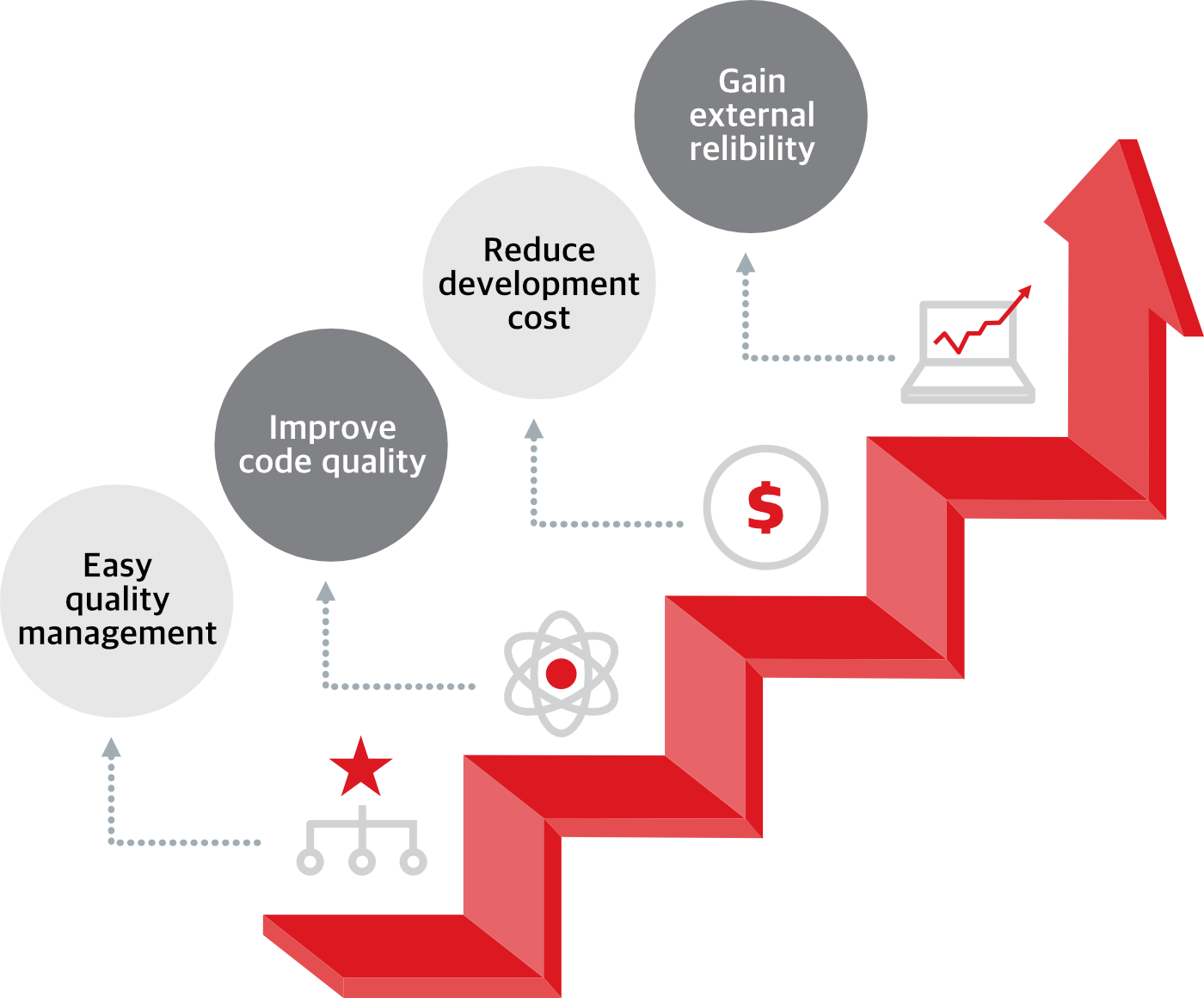
This static application security tool, CODEMIND detects security weaknesses hidden in software source code and detects runtime errors in advance.
As a cutting-edge technology that detects all execution paths without running software, it is an essential element for securing software safety and security.
downloadbrochure
CSI/CQI SERVER SYSTEM
- Configuration management system such as SVN support
- User direct upload analysis
- Provid a web-based management system
- Developer, administrator, and user authority Management
- Automatic/manual analysis Control
ANALYSIS FEATURES
- Execution error detection
- Defective code detection
- Apply the latest summary analysis framework
- The optimized value analysis engine
- The highest performance memory analysis engine
- Procedures analysis at high speed
- High speed the use of machine learning techniques
- Selectable for options for analysis speed and accuracy
Major rules of CODEMIND CSI
(Secure Coding Inspection)
(Secure Coding Inspection)
- SQL Injection
- Resource Injection
- Cross-site Script
- OS Command Injection
- LDAP Injection
- Cross-site Request Forgery
- Relative/Absolute Path Traversal
- Integer Overflow
- Weak Encryption
- Hard-coded Password
- Null Pointer Dereference
- Data Leak between Sessions
- Information Leak of System Data
- Improper Resource Shutdown/Release
- API abuse
Major rules of CODEMIND CQI
(Code Quality Inspection)
(Code Quality Inspection)
- Buffer Overrun/Underrun
- Use after Free
- Unused Value
- Unreachable Code
- Incorrect Numeric Casting
- Uninitialized Variable
- Type Overrun/Underrun
- Null Pointer Dereference
- Memory Leak
- Double Free
- Divide by Zero
- Return Pointer to Local
- Null Check after Dereference
- Mismatched Memory Management
Why CODEMIND?